This tool demonstrates the power of UAC bypasses and built-in features of Windows. This utility auto-locates winlogon.exe, steals and impersonates it's process TOKEN, and spawns a new SYSTEM-level process with the stolen token. Combined with UAC bypass method #41 (ICMLuaUtil UAC bypass) from hfiref0x's UACME utility, this utility can auto-elevate a low privileged Administrative account to NT AUTHORITY\SYSTEM.
The following image demonstrates using UACME combined with Auto-Elevate to go from a low-privileged Administrator account to NT AUTHORITY\SYSTEM on Windows 10 21H1.
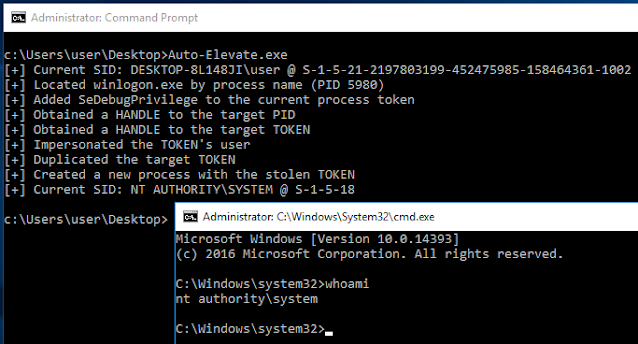
The following image demonstrates escalation from a high-privileged Administrator account to SYSTEM without a UAC bypass
Technical Explanation
The following steps are performed by Auto-Elevate to escalate from a low-privileged Administrator to SYSTEM:
Auto-Elevate
- The winlogon.exe process is located by enumerating the systems running processes with CreateToolhelp32Snapshot, Process32First, and Process32Next
- SeDebugPrivilege is enabled for the current process via a call to AdjustTokenPrivileges, as it's required to open a HANDLE to winlogon.exe
- A handle to the winlogon.exe process is opened by calling OpenProcess, for this call PROCESS_ALL_ACCESS is used (however, it's overkill)
- A handle to winlogon's process token is retrieved by calling OpenProcessToken combined with the previously obtained process handle
- The user (SYSTEM) of winlogon is impersonated by calling ImpersonateLoggedOnUser
- The impersonated token handle is duplicated by calling DuplicateTokenEx with SecurityImpersonation, this creates a duplicated token we can use
- Using the duplicated, and impersonated token a new CMD instance is spawned by calling CreateProcessWithTokenW
To-Do
MITRE ATT&CK Mapping
- Token Manipulation: T1134
- Access Token Manipulation: Token Impersonation/Theft: T1134.001
- Access Token Manipulation: Create Process with Token: T1134.002
- Access Token Manipulation: Make and Impersonate Token: T1134.003
You may be interested in:
>> Is a Chromebook worth replacing a Windows laptop?
>> Find out in detail the outstanding features of Google Pixel 4a
>> Top 7 best earbuds you should not miss
Related Posts:
>> Recognizing 12 Basic Body Shapes To Choose Better Clothes
>>Ranking the 10 most used smart technology devices
>> Top 5+ Best E-readers: Compact & Convenient Pen




0 Comments:
Post a Comment