Rip Raw is a small tool to analyse the memory of compromised Linux systems. It is similar in purpose to Bulk Extractor, but particularly focused on extracting system Logs from memory dumps from Linux systems. This enables you to analyse systems without needing to generate a profile.
This is not a replacement for tools such as Rekall and Volatility which use a profile to perform a more structured analysis of memory.
Rip Raw works by taking a Raw Binary such as a Memory Dump and carves files and logs using:
-
Text/binary boundaries
-
File headers and file magic
-
Log entries
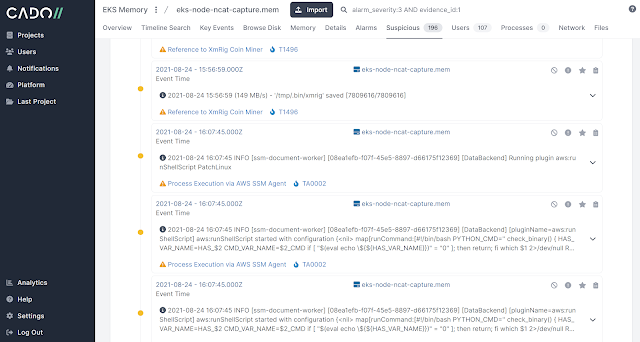
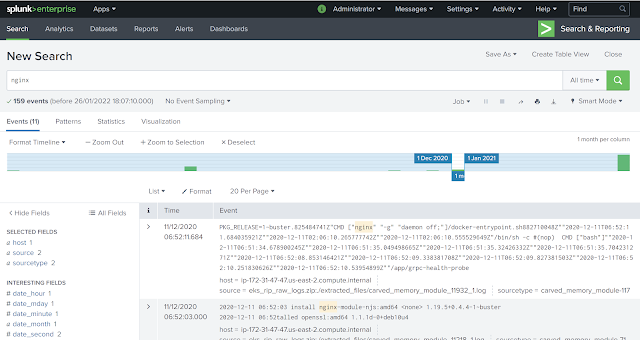
Then puts them in a zip file for secondary processing by other tools such as Cado Response or a SIEM such as Splunk (examples below).
Example
For example, after capturing the memory of an Amazon EKS ( Elastic Kubernetes Service) system compromised with a crypto-mining worm we processed it with rip_raw:
python3 rip_raw.py -f eks-node-ncat-capture.mem And then the large zip of logs that Rip Raw outputs can be viewed in a tool such as Cado Response (below). Approximately 36500 log events were extracted from this memory image, along with a number of binaries such as images and executables.
Learn More
You may be interested in:
>> Is a Chromebook worth replacing a Windows laptop?
>> Find out in detail the outstanding features of Google Pixel 4a
>> Top 7 best earbuds you should not miss
Related Posts:
>> Recognizing 12 Basic Body Shapes To Choose Better Clothes
>>Ranking the 10 most used smart technology devices
>> Top 5+ Best E-readers: Compact & Convenient Pen

0 Comments:
Post a Comment