Check out our RPC Firewall blog post to gain better understanding of RPC, RPC attacks and the solution: the RPC Firewall. For any questions, issues, or simlpy to shout out - we would love to hear from you! Contact us at [email protected]
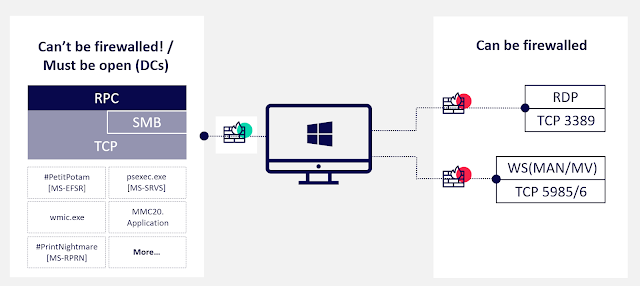
RPC is the underlying mechanism which is used for numerous lateral movement techniques, reconnaisense, relay attacks, or simply to exploit vulnerable RPC services.
DCSync attack? over RPC. Remote DCOM? over RPC. WMIC? over RPC. SharpHound? over RPC. PetitPotam? over RPC. PsExec? over RPC. ZeroLogon? over RPC... well, you get the idea :)
Research
Install the RPC Firewall and configure it to audit all remote RPC calls. Once executing any remote attack tools, you will see which RPC UUIDs and Opnums were called remotely.
Remote RPC Attacks Detection
When the RPC Firewall is configured to audit, it write events to the Windows Event Log.
Forward this log to your SIEM, and use it to create baselines of remote RPC traffic for your servers.
Once an abnormal RPC call is audited, use it to trigger an alert for your SOC team.
Remote RPC Attacks Protection
The RPC Firewall can be configured to block & audit only potentially malicious RPC calls. All other RPC calls are not audited to reduce noise and improve performance.
Once a potentially malicious RPC call is detected, it is blocked and audited. This could be used to alert your SOC team, while keeping your servers protected.
It is made up from 3 components:
- RpcFwManager.exe - In charge of managing the RPC Firewall.
- RpcFirewall.dll - Injected DLL which performs the audit & filtering of RPC calls.
- RpcMessages.dll - A common library for sharing functions, and logic that writes data into Windows Event Viewer.
Installing / Uninstalling
Installation simply drops the RPC Firewall DLLs into the %SystemRoot%\System32, and configures the RPCFWP application log for the Event Viewer.
RpcFwManager.exe /installUninstalling does the opposite.
RpcFwManager.exe /uninstallProtecting Process(es)
The RpcFwManager tried to inject the rpcFirewall.dll only to processes which have the RPCRT4.DLL loaded into them.
Once the rpcFirewall.dll is loaded, it verifies that the host process has a valid RPC interface, and is listening for remote connections.
Otherwise, the rpcFirewall.dll unloaded itself from the target process.
If the process is a valid RPC server, the rpcFirewall starts to audit & monitor incoming RPC calls, according to the configuration file.
To protect a single process by pid:
RpcFwManager.exe /pid <pid>To protect a single process by name:
RpcFwManager.exe /process <process name>To protect all process, simply leave the or parametes blank.
RpcFwManager.exe /process
RpcFwManager.exe /pidUnprotecting Processes
To disable the RPC Firewall, either uninstall it, or use the unprotect parameter:
RpcFwManager.exe /unprotectThis will unload the rpcFirewall.dll from all processes.
Configuration
The rpcFwManager.exe looks for a RpcFw.conf file, in the same directory of the executable. This file uses the following configuration options:
- uuid -> match a specific uuid
- opnum -> match a RPC opnum
- addr -> match a remote IP address
- action -> can be either allow or block (default allow)
- audit -> true or false, controls whether events are written to the RPCFWP log (default false)
- verbose -> when true, outputs debug informaiton for specific RPC calls (default false)
The configuration order is important, as the first match determines the outcome of the RPC call.
For example, the following configuration will protect a DC from a DCSync attack by disabling the MS-DRSR UUID from non-domain machines. Also, notice that audit is enabled only for blocked MS-DRSR attempts, which could alert your SOC to a potential attack!
uuid:e3514235-4b06-11d1-ab04-00c04fc2dcd2 addr:<dc_addr1> action:allow
uuid:e3514235-4b06-11d1-ab04-00c04fc2dcd2 addr:<dc_addr2> action:allow
uuid:e3514235-4b06-11d1-ab04-00c04fc2dcd2 action:block audit:trueWhenever the configuration changes, you need to notify the rpcFirewall.dll via the update command:
RpcFwManager.exe /updateYes! Don't be shy to do a pull request.
We want this also! please reach out to us with any thoughts, ideas or issues you are having: [email protected]
For more details see LICENSE.
You may be interested in:
>> Is a Chromebook worth replacing a Windows laptop?
>> Find out in detail the outstanding features of Google Pixel 4a
>> Top 7 best earbuds you should not miss
Related Posts:
>> Recognizing 12 Basic Body Shapes To Choose Better Clothes
>>Ranking the 10 most used smart technology devices
>> Top 5+ Best E-readers: Compact & Convenient Pen

0 Comments:
Post a Comment