1) A binary operation on a set of integers is defined as y = x2 + y2. Which one of the following statements is TRUE about?
- Commutative but not associative
- Both commutative and associative
- Associative but not commutative
- Neither commutative nor associative
Answer: a
Explanation:
Associativity:
A binary operation ∗ on a set S is said to be associative if it satisfies the
a ∗ (b ∗ c) = (a ∗ b) ∗ c for all a, b, c ∈S.
Commutativity:
A binary operation ∗ on a set S is said to be commutative if it satisfies the condition:
a ∗ b = b ∗ a for all a, b, ∈ S.
In this case, the order in which elements are combined does not matter.
Solution:
Here a binary operation on a set of integers is defined as x ⊕ y = x2 + y2.
for Commutativity: x ⊕ y = y ⊕ x.
LHS => x ⊕ y = x^2 + y^2
RHS => y ⊕ x = y^2 + x^2
LHS = RHS. hence commutative.
for Associativity: x ⊕ (y ⊕ z) =(x ⊕ y) ⊕ z
LHS => x ⊕ (y ⊕ z) = x ⊕ ( y^2 + z^2) = x^2 + (y^2 + z^2) ^ 2
RHS => (x ⊕y ) ⊕ z = ( x^2 + y^2) ⊕ z = (x^2 + y^2) ^ 2 + z^2
So, LHS ≠ RHS, hence not associative.
Another Solution :
commutative as xy is always same as yx.
is not associative as (xy)z is (x^2 + y^2)^2 + z^2, but x(yz) is x^2 + (y^2 + z^2)^2.
2) Which one of the following does NOT equal to
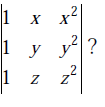
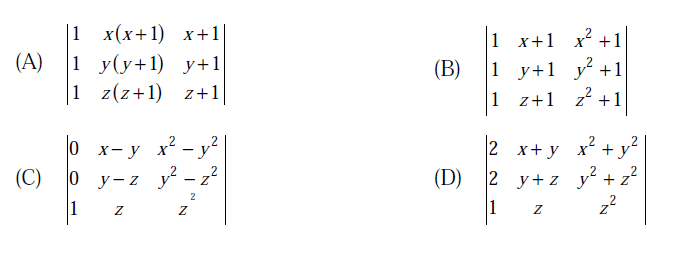
Answer: a
Explanation:
First of all, you should know the basic properties of determinants before approaching
For these kind of problems.
1) Applying any row or column transformation does not change the determinant
2) If you interchange any two rows, sign of the determinant will change
A = | 1 x x^2 |
| 1 y y^2 |
| 1 z z^2 |
To prove option (b)
=> Apply column transformation C2 -> C2 + C1
C3 -> C3 + C1
=> det(A) = | 1 x + 1 x^2 + 1 |
| 1 y + 1 y^2 + 1 |
| 1 z + 1 z^2 + 1 |
To prove option (c),
=> Apply row transformations R1 -> R1 - R2
R2 -> R2 - R3
=> det(A) = | 0 x - y x^2 - y^2 |
| 0 y - z y^2 - z^2 |
| 1 z z^2 |
To prove option (d),
=> Apply row transformations R1 -> R1 + R2
R2 -> R2 + R3
=> det(A) = | 2 x + y x^2 + y^2 |
| 2 y + z y^2 + z^2 |
| 1 z z^2 |
3) The smallest integer that can be represented by an 8-bit number in 2's complement form is
- -256
- -128
- -127
- 0
Answer: b
Explanation:
Two's complement is a mathematical operation on binary numbers, and is an example of a radix complement. It is used in computing as a method of signed number representation.
The two's complement of an N-bit number is defined as its complement with respect to 2N; the sum of a number and its two's complement is 2N. For instance, for the three-bit number 0102, the two's complement is 1102, because 0102 + 1102 = 10002 = 810 which is equal to 23. The two's complement is calculated by inverting the bits and adding one.
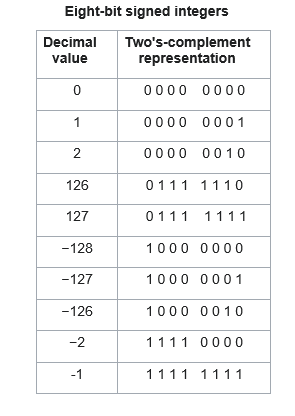
For n bit 2's complement numbers, range of number is -(2(n-1)) to +(2 (n-1) -1)
4) In the following truth table, V = 1 if and only if the input is valid.
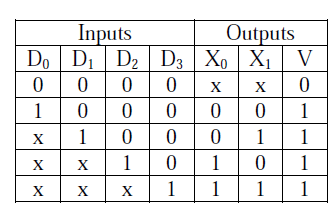
What function does the truth table represent?
- Priority encoder
- Decoder
- Multiplexer
- Demultiplexer
Answer: a
Explanation:
Since there are more than one outputs and number of outputs is less than inputs, it is a Priority encoder
V=1 when input is valid and for priority encoder it checks first high bit encountered. Except all are having at least one bit high and 'x' represents the "don't care" as we have found a high bit already. So answer is (A).
5) Which one of the following is the tightest upper bound that represents the number of swaps required to sort n numbers using selection sort?
- O(log n)
- O(n)
- O(nLogn)
- O(n^2)
Answer: b
Explanation: To sort elements in increasing order, selection sort always picks the maximum element from remaining unsorted array and swaps it with the last element in the remaining array. So the number of swaps, it makes in n-1 which is O(n)
6) Which one of the following is the tightest upper bound that represents the time complexity of inserting an object into a binary search tree of n nodes?
- O(1)
- O(Logn)
- O(n)
- O(nLogn)
Answer: c
Explanation: To insert an element, we need to search for its place first. The search operation may take O(n) for a skewed tree like following.
To insert 50, we will have to traverse all nodes.
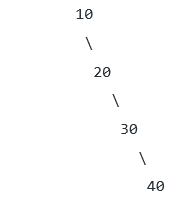
7) Consider the languages L1 = Φ and L2 = {a}. Which one of the following represents L1 L2* U L1*

Answer: a
Explanation:
: L1 L2* U L1*
Result of L1 L2* is Φ.
{ Φ} indicates an empty language. Concatenation of Φ with any other language is Φ. It works as 0 in multiplication.
L1* = Φ* which is { ε }.
Union of Φ and { ε } is { ε }
8) What is the maximum number of reduce moves that can be taken by a bottom-up parser for a grammar with no epsilon- and unit-production (i.e., of type A -> ? and A -> a) to parse a string with n tokens?
- n/2
- n-1
- 2n-1
- 2n
Answer: c
Explanation:
Given in the question, a grammar with no epsilon- and unit-production (i.e., of type A -> ? and A -> a).
To get maximum number of Reduce moves, we should make sure than in each sentential form only one terminal is reduced. Since there is no unit production, so last 2 tokens will take only 1 move.
So To Reduce input string of n tokens, first Reduce n-2 tokens using n-2 reduce moves and then Reduce last 2 tokens using production which has . So total of n-2+1 = n-1 Reduce moves.
Suppose the string is abcd. ( n = 4 ).
We can write the grammar which accepts this string as follows:
S -> aB
B -> bC
C -> cd
The Right Most Derivation for the above is:
S -> aB ( Reduction 3 )
-> abC ( Reduction 2 )
-> abcd ( Reduction 1 )
We can see here that no production is for unit or epsilon. Hence 3 reductions here.
We can get less number of reductions with some other grammar which also does't produce unit or epsilon productions,
S -> abA
A-> cd
The Right Most Derivation for the above as:
S -> abA ( Reduction 2 )
-> abcd ( Reduction 1 )
Hence 2 reductions.
But we are interested in knowing the maximum number of reductions which comes from the 1st grammar. Hence total 3 reductions as maximum, which is ( n - 1) as n = 4 here.
Thus, Option B.
9) A scheduling algorithm assigns priority proportional to the waiting time of a process. Every process starts with priority zero (the lowest priority). The scheduler re-evaluates the process priorities every T time units and decides the next process to schedule. Which one of the following is TRUE if the processes have no I/O operations and all arrive at time zero?
- This algorithm is equivalent to the first-come-first-serve algorithm
- This algorithm is equivalent to the round-robin algorithm.
- This algorithm is equivalent to the shortest-job-first algorithm..
- This algorithm is equivalent to the shortest-remaining-time-first algorithm
Answer: b
Explanation: The scheduling algorithm works as round robin with quantum time equals to T. After a process's turn comes and it has executed for T units, its waiting time becomes least and its turn comes again after every other process has got the token for T units.
10) Match the problem domains in GROUP I with the solution technologies in GROUP II

- P - 1, Q - 2, R - 3, S - 4
- P - 3, Q - 4, R - 2, S - 1
- P - 3, Q - 1, R - 4, S - 2
- P - 4, Q - 3, R - 2, S - 1
Answer: c
Explanation: The answer can be easily guessed with XML. XML is used for information representation.
11) Three concurrent processes X, Y, and Z execute three different code segments that access and update certain shared variables. Process X executes the P operation (i.e., wait) on semaphores a, b and c; process Y executes the P operation on semaphores b, c and d; process Z executes the P operation on semaphores c, d, and a before entering the respective code segments. After completing the execution of its code segment, each process invokes the V operation (i.e., signal) on its three semaphores. All semaphores are binary semaphores initialized to one. Which one of the following represents a deadlock-free order of invoking the P operations by the processes?
- X: P( a )P( b )P( c ) Y: P( b )P( c )P( d ) Z: P( c )P( d )P( a )
- X: P( b )P( a )P( c ) Y: P( b )P( c )P( d ) Z: P( a )P( c )P( d )
- X: P( b )P( a )P( c ) Y: P( c )P( b )P( d ) Z: P( a )P( c )P( d )
- X: P( a )P( b )P( c ) Y: P( c )P( b )P( d ) Z: P( c )P( d )P( a )
Answer: b
Explanation:
Option A can cause deadlock. Imagine a situation process X has acquired a, process Y has acquired b and process Z has acquired c and d. There is circular wait now.
Option C can also cause deadlock. Imagine a situation process X has acquired b, process Y has acquired c and process Z has acquired a. There is circular wait now.
Option D can also cause deadlock. Imagine a situation process X has acquired a and b, process Y has acquired c. X and Y circularly waiting for each other.
Consider option A) for example here all 3 processes are concurrent so X will get semaphore a, Y will get b and Z will get c, now X is blocked for b, Y is blocked for c, Z gets d and blocked for a. Thus it will lead to deadlock.
Similarly one can figure out that for B) completion order is Z, X then Y.
12) Which of the following statements is /are FALSE?
1) For every non-deterministic Turing machine, there exists an equivalent deterministic Turing machine.
2) Turing recognizable languages are closed under union and complementation.
3) Turing decidable languages are closed under intersection and complementation.
4) Turing recognizable languages are closed under union and intersection.
- 1 and 4 only
- 1 and 3 only
- 2 only
- 3 only
Answer: c
Explanation:
A recognizer of a language is a machine that recognizes that language.
A decider of a language is a machine that decides that language.
Both types of machine halt in the Accept state on strings that are in the language
A Decider also halts if the string is not in the language
A Recogizer MAY or MAY NOT halt on strings that are not in the language
On all input:
A Decider MUST halt (in Accept or Reject state)
A Recogizer MAY or MAY NOT halt on some strings (Q: Which ones?)
A language is Turing-decidable (or decidable) if some Turing machine decides it. Aka Recursive Language.
A language is Turing-recognizable if some Turing machine recognizes it. Aka Recursively Enumerable Language.
Recursive (Turing Decidable) languages are closed under following
Kleene star, concatenation, union, intersection, complement and set difference.
Recursively enumerable language are closed under Kleene star, concatenation, union, intersection. They are NOT closed under complement or set difference.
13) Which of the following statements are TRUE?
1. The problem of determining whether there exists a cycle in an undirected graph is in P.
2. The problem of determining whether there exists a cycle in an undirected graph is in NP.
3. If a problem A is NP-Complete, there exists a non-deterministic polynomial time algorithm to solve A.
- 1, 2 and 3
- 1 and 2 only
- 2 and 3 only
- 1 and 3 only
Answer: a
Explanation:
- We can either use BFS or DFS to find whether there is a cycle in an undirected graph. For example, see DFS based implementation to detect cycle in an undirected graph. The time complexity is O(V + E) which is polynomial.
- If a problem is in P, then it is definitely in NP (can be verified in polynomial time). See NP-Completeness
- True. NP-Completeness
14) What is the time complexity of Bellman-Ford single-source shortest path algorithm on a complete graph of n vertices?
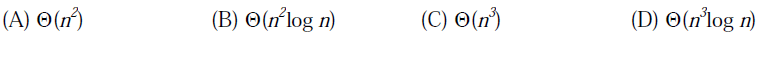
Answer: c
Explanation: Time complexity of Bellman-Ford algorithm is O(VE) where V is number of vertices and E is number of edges. For a complete graph with n vertices, V = n, E = O(n^2). So overall time complexity becomes O(n^3)
15) In a k-way set associative cache, the cache is divided into v sets, each of which consists of k lines. The lines of a set are placed in sequence one after another. The lines in set s are sequenced before the lines in set (s+1). The main memory blocks are numbered 0 onwards. The main memory block numbered j must be mapped to any one of the cache lines from.
- (j mod v) * k to (j mod v) * k + (k - 1)
- (j mod v) to (j mod v) + (k - 1)
- (j mod k) to (j mod k) + (v - 1)
- (j mod k) * v to (j mod k) * v + (v - 1)
Answer: a
Explanation:
Number of sets in cache = v. So, main memory block j will be mapped to set (j mod v), which will be any one of the cache lines from (j mod v) * k to (j mod v) * k + (k - 1).
(Associativity plays no role in mapping- k-way associativity means there are k spaces for a block and hence reduces the chances of replacement.)
16) Which one of the following expressions does NOT represent exclusive NOR of x and y?
- xy + x'y'
- x ⊕ y'
- x' ⊕ y
- x' ⊕ y'
Answer: d
Explanation:

Option-C is also correct.
Option-D x'⊕y' = x"y' + x'y" = xy' + x'y = x⊕y ≠ x⊙y
Therefore option (D) is false.
17) Which one of the following functions is continuous at x = 3?
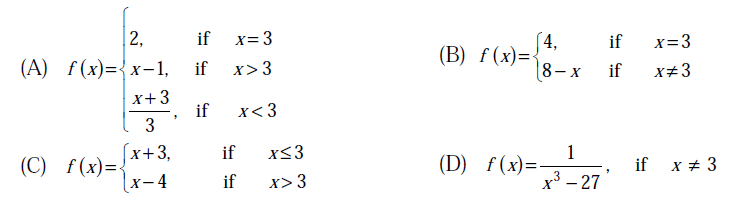
Answer: a
Explanation:
A function is continuous at some point c,
Value of f(x) defined for x > c = Value of f(x) defined for x < c = Value of f(x) defined for x = c
All values are 2 in option A
18) Function f is known at the following points:
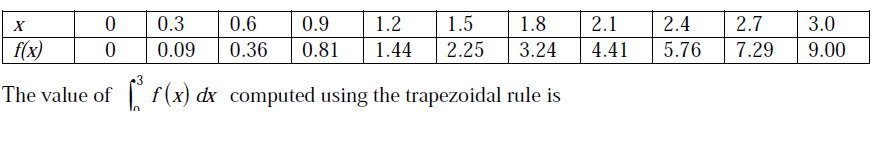
- 8.983
- 9.003
- 9.017
- 9.045
Answer: d
Explanation:
Trapezoidal Rule
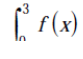
dx = h/2[(y0 - yn) +2(y1 + y2+ . . . . . . . . . . . . + yn-1)
Where h = b - a/n
Here y0, yn => extreme ordinates
a = lower limit
b = upper limit
here h = 3 - 0 / 10 = 0.3 (width)
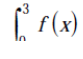
dx = 0.3 / 2 [(0 + 9) +2(0.009 + 0.36 + . . . . . . . . . . . . . . . . . . . . . . . . . . . . + 7.29)]
= 0.3 / 2 [ 9 + 2(25.65)]
= 0.3 / 2 [ 9 + 51.3]
= 9.045
Answers :- Option(D)
Since the intervals are uniform, apply the uniform grid formula of trapezoidal rule.
19) Consider an undirected random graph of eight vertices. The probability that there is an edge between a pair of vertices is 1 / 2. What is the expected number of unordered cycles of length three?
- 1 / 8
- 1
- 7
- 8
Answer: c
Explanation: A cycle of length 3 can be formed with 3 vertices. There can be total 8C3 ways to pick 3 vertices from 8. The probability that there is an edge between two vertices is 1/2. So expected number of unordered cycles of length 3 = (8C3) * (1 / 2) ^ 3 = 7
20) Which of the following statements is/are TRUE for undirected graphs?
P: Number of odd degree vertices is even.
Q: Sum of degrees of all vertices is even.
- P only
- Q only
- Both P and Q
- Neither P nor Q
Answer: c
Explanation:
P is true for undirected graph as adding an edge always increases degree of two vertices by 1.
Q is true: If we consider sum of degrees and subtract all even degrees, we get an even number because every edge increases the sum of degrees by 2. So total number of odd degree vertices must be even.
21) The line graph L(G) of a simple graph G is defined as follows:
There is exactly one vertex v(e) in L(G) for each edge e in G.
For any two edges e and e' in G, L(G) has an edge between v(e) and v(e'), if and only if e and e' are incident with the same vertex in G.
Which of the following statements is/are TRUE?
(P) The line graph of a cycle is a cycle.
(Q) The line graph of a clique is a clique.
(R) The line graph of a planar graph is planar.
(S) The line graph of a tree is a tree.
- P only
- P and R only
- R only
- P, Q and S only
Answer: a
Explanation: In the mathematical discipline of graph theory, the line graph of an undirected graph G is another graph L(G) that represents the adjacencies between edges of G. L(G) is constructed in the following way: for each edge in G, make a vertex in L(G); for every two edges in G that have a vertex in common, make an edge between their corresponding vertices in L(G).
22) What is the logical translation of the following statement?
"None of my friends are perfect."

Answer: d
Explanation:

F(x) ==> x is my friend
P(x) ==> x is perfect
D is the correct answer.
A. There exist some friends which are not perfect
B. There are some people who are not my friend and are perfect
C. There exist some people who are not my friend and are not perfect.
D. There doesn't exist any person who is my friend and perfect
23) Consider the following sequence of micro-operations.
MBR ← PC
MAR ← X
PC ← Y
Memory ← MBR
Which one of the following is a possible operation performed by this sequence?
- Instruction fetch
- Operand fetch
- Conditional branch
- Initiation of interrupt service
Answer: d
Explanation:
MBR - Memory Buffer Register ( that stores the data being transferred to and from the immediate access store)
MAR - Memory Address Register ( that holds the memory location of data that needs to be accessed.)
PC - Program Counter ( It contains the address of the instruction being executed at the current time )
The 1st instruction places the value of PC into MBR
The 2nd instruction places an address X into MAR.
The 3rd instruction places an address Y into PC.
The 4th instruction places the value of MBR ( which was the old PC value) into Memory.
Now it can be seen from the 1st and the 4th instructions, that the control flow was not sequential and the value of PC was stored in the memory, so that the control can again come back to the address where it left the execution.
This behaviour is seen in the case of interrupt handling. And here X can be the address of the location in the memory which contains the beginning address of Interrupt service routine.
And Y can be the beginning address of Interrupt service routine.
In case of conditional branch (as for option C ) only PC is updated with the target address and there is no need to store the old PC value into the memory.
And in the case of Instruction fetch and operand fetch ( as for option A and B), PC value is not stored anywhere else.
Hence option D.
24) Consider a hard disk with 16 recording surfaces (0 - 15) having 16384 cylinders (0 - 16383) and each cylinder contains 64 sectors (0 - 63). Data storage capacity in each sector is 512 bytes. Data are organized cylinder-wise and the addressing format is . A file of size 42797 KB is stored in the disk and the starting disk location of the file is 1200, 9, 40>. What is the cylinder number of the last sector of the file, if it is stored in a contiguous manner?
- 1281
- 1282
- 1283
- 1284
Answer: d
Explanation:
File size is 42797KB = 4279 * 2 ^ 10B = 85594 * 2 ^ 9B.
Now one sector = 512B
so file will be stored in 85594 sectors i.e. we need to cross 85594 sectors
starting of the file is
number of cylinders to cross = 85594 / 16 * 64 = 83 cylinders
remaining sectors to cross = 85594 - (83 * 16 * 64) = 602
number of surfaces to cross = 9
so to cross 9 surface we need to cross on more cylinder as file has started at surface 9 and no of surface in cylinder is 16 so
number of cylinder to cross = 83 + 1 = 84
so cylinder no. 1200 + 84 = 1284
25) The number of elements that can be sorted in (log n) time using heap sort is

Answer: c
Explanation:
Time Complexity of the heapify() Method
Let's start with the heapify() method since we also need it for the heap's initial build.
In the heapify() function, we walk through the tree from top to bottom. The height of a binary tree (the root not being counted) of size n is log2 n at most, i.e., if the number of elements doubles, the tree becomes only one level deeper:
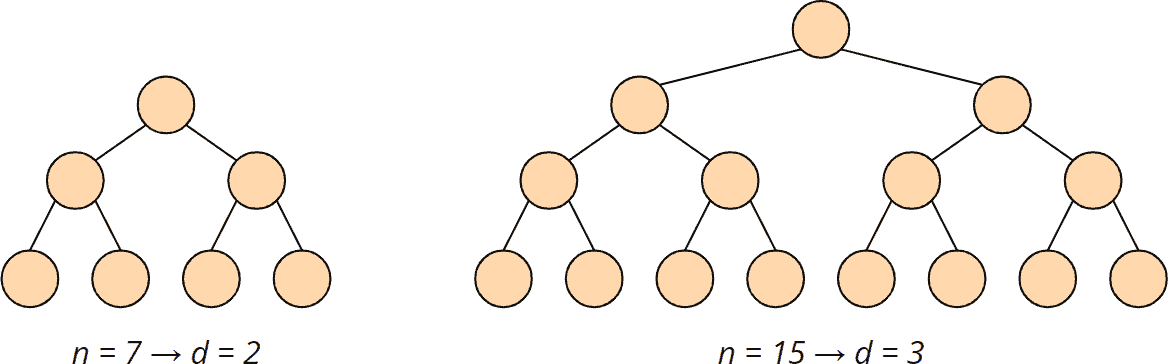
The complexity for the heapify() function is accordingly O(log n).
Time Complexity of the buildHeap() Method
To initially build the heap, the heapify() method is called for each parent node - backward, starting with the last node and ending at the tree root.
A heap of size n has n / 2 (rounded down) parent nodes:
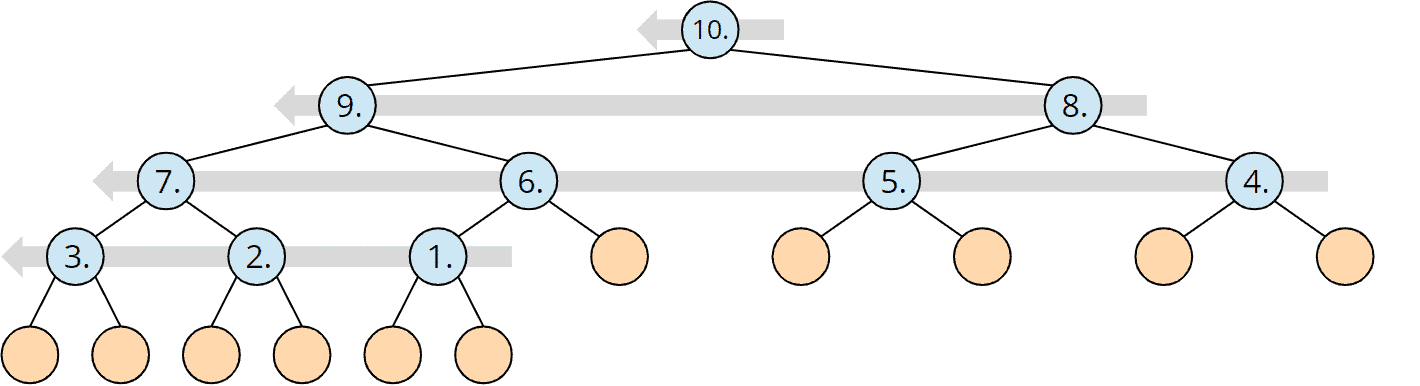
Since the complexity of the heapify() method is O(log n) as shown above, the complexity for the buildHeap() method is, therefore, maximum* O(n log n).
* In the section after the next one, I will show that the time complexity of the buildHeap() method is actually O(n). Since this does not change the overall time complexity, it is not mandatory to perform this in-depth analysis.
Total Time Complexity of Heapsort
The heapify() method is called n - 1 times. So the total complexity for repairing the heap is also O(n log n).
Both sub-algorithms, therefore, have the same time complexity. Hence:
The time complexity of Heapsort is: O(n log n)
26) Consider the following function:
- ⊝(n2)
- ⊝(n2 Logn)
- ⊝(n3)
- ⊝(n3 Logn)
Answer: b
Explanation: Here we have to tell the value of k returned not the time complexity.
The outer loop runs n / 2 times
The inner loop runs logn times.(2 ^ k = n => k = logn).
Now looking at the value of k in inner loop, n is added to k, logn times as the inner loop is running logn times.
Therefore total time complexity is inner multiplied with outer loop complexity which (n for outer and nlogn for inner) n * logn.
Therefore the value of k after running the inner loop one time is n ^ 2logn.
27) Consider the following languages.
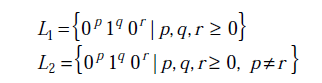
Which one of the following statements is FALSE?
- L2 is context-free.
- L1 intersection L2 is context-free.
- Complement of L2 is recursive.
- Complement of L1 is context-free but not regular.
Answer: d
Explanation:
(D) is false.
L1 is regular, so its complement would also be regular.
L1 is a regular language of the form 0^* 1^* 0^*. L2 on the other hand is a CFL as it can be derived from the following CFG
L2 = { 0^p 1^q 0^r | p, q, r > 0 And p notEqualTo r }
S -> AC | CA
C -> 0C0 | B
A -> 0A | 0
B -> 1B | epsilon
If coming up with a CFG for L2 is difficult, one can intuitively see that by reducing it to a simpler problem. L2 is very similar to a known CFL L3 = { a^m b^l | m notEqualTo n }
(A) L2 is context free, which is true [CORRECT]
(B) L1 intersection L2 is context free, which is again true because L1 is a regular language and L2 is a CFL. RL union CFL is always a CFL. Hence [CORRECT]
(C) Complement of L2 is recursive, which is true due to the fact that complement of a CFL is CSL for sure (Context sensitive language), which in turn (CSL) is a subset of recursive languages. Hence [CORRECT]
(D) Complement of L1 is context free but not regular, which is false due to closure laws of regular languages. Complement of a RL is always a RL. Hence [INCORRECT]
28) Consider the DFA given.
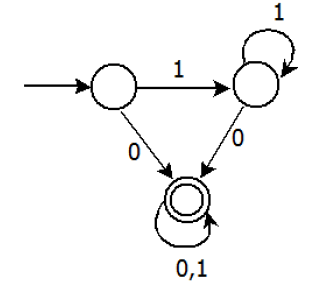
Which of the following are FALSE?
1. Complement of L(A) is context-free.
2. L(A) = L((11 * 0 + 0)(0 + 1) * 0 * 1 *)
3. For the language accepted by A, A is the minimal DFA.
4. A accepts all strings over {0, 1} of length at least 2.
- 1 and 3 only
- 2 and 4 only
- 2 and 3 only
- 3 and 4 only
Answer: d
Explanation:
1 is true. L(A) is regular, its complement would also be regular. A regular language is also context free.
2 is true.
3 is false, the DFA can be minimized to two states. Where the second state is final state and we reach second state after a 0.
4 is clearly false as the DFA accepts a single 0.
29) A shared variable x, initialized to zero, is operated on by four concurrent processes W, X, Y, Z as follows. Each of the processes W and X reads x from memory, increments by one, stores it to memory, and then terminates. Each of the processes Y and Z reads x from memory, decrements by two, stores it to memory, and then terminates. Each process before reading x invokes the P operation (i.e., wait) on a counting semaphore S and invokes the V operation (i.e., signal) on the semaphore S after storing x to memory. Semaphore S is initialized to two. What is the maximum possible value of x after all processes complete execution?
- -2
- -1
- 1
- 2
Answer: d
Explanation:
A critical section in which the process may be changing common variables, updating table, writing a file and perform another function. The important problem is that if one process is executing in its critical section, no other process is to be allowed to execute in its critical section. Each process must request permission to enter its critical section. A semaphore is a tool for synchronization and it is used to remove the critical section problem which is that no two processes can run simultaneously together so to remove this two signal operations are used named as wait and signal which is used to remove the mutual exclusion of the critical section. as an unsigned one of the most important synchronization primitives, because you can build many other Decrementing the semaphore is called acquiring or locking it, incrementing is called releasing or unlocking.
Solution :
Since initial value of semaphore is 2, two processes can enter critical section at a time- this is bad and we can see why.
Say, X and Y be the processes. X increments x by 1 and Z decrements x by 2. Now, Z stores back and after this X stores back. So, final value of x is 1 and not -1 and two Signal operations make the semaphore value 2 again. So, now W and Z can also execute like this and the value of x can be 2 which is the maximum possible in any order of execution of the processes. (If the semaphore is initialized to 1, processed would execute correctly and we get the final
value of x as -2.)
Option (D) is the correct answer.
Another Solution:
Processes can run in many ways, below is one of the cases in which x attains max value Semaphore S is initialized to 2
Process W executes S = 1, x = 1 but it doesn't update the x variable.
Then process Y executes S = 0, it decrements x, now x = -2 and signal semaphore S = 1
Now process Z executes s = 0, x = -4, signal semaphore S = 1
Now process W updates x = 1, S = 2 Then process X executes X = 2
So correct option is D
Another Solution:
S is a counting semaphore initialized to 2 i.e., Two process can go inside a critical section protected by S. W, X read the variable, increment by 1 and write it back. Y, Z can read the variable, decrement by 2 and write it back.
Whenever Y or Z runs the count gets decreased by 2. So, to have the maximum sum, we should copy the variable into one of the processes which increases the count, and at the same time the decrementing processed should run parallel, so that whatever they write back into memory can be overridden by incrementing process. So, in effect decrement would never happen.
30) In an IPv4 datagram, the M bit is 0, the value of HLEN is 10, the value of total length is 400 and the fragment offset value is 300. The position of the datagram, the sequence numbers of the first and the last bytes of the payload, respectively are
- Last fragment, 2400 and 2789
- First fragment, 2400 and 2759
- Last fragment, 2400 and 2759
- Middle fragment, 300 and 689
Answer: c
Explanation:
M = 0 indicates that this packet is the last packet among all fragments of original packet. So the answer is either A or C.
It is given that HLEN field is 10. Header length is number of 32 bit words. So header length = 10 * 4 = 40
Also, given that total length = 400.
Total length indicates total length of the packet including header.
So, packet length excluding header = 400 - 40 = 360
Last byte address = 2400 + 360 - 1 = 2759 (Because numbering starts from 0)
31) The following figure represents access graphs of two modules M1 and M2. The filled circles represent methods and the unfilled circles represent attributes. If method m is moved to module M2 keeping the attributes where they are, what can we say about the average cohesion and coupling between modules in the system of two modules?
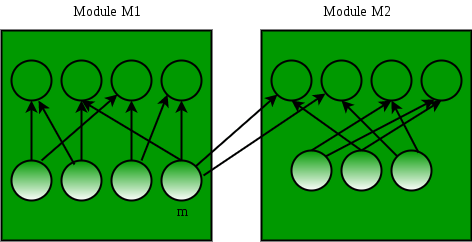
- There is no change.
- Average cohesion goes up but coupling is reduced.
- Average cohesion goes down and coupling also reduces.
- Average cohesion and coupling increase.
Answer: a
Explanation:
Answer is "No Change"
Cohesion refers to the degree to which the elements of a module belong together.
Coupling is the manner and degree of interdependence between software modules
Coupling between M1 and M2 = (Number of external links) /
(Number of modules)
= 2 / 2
= 1Cohesion of a module = (Number of internal links) / (Number of methods)
Cohesion of M1 = 8 / 4 = 2
Cohesion of M2 = 6 / 3 = 2
After moving method m to M2, we get following
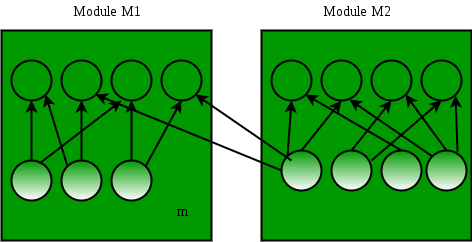
Coupling = 2 / 2 = 1
Cohesion of M1 = 6 / 3 = 2
Cohesion of M2 = 8 / 4 = 2
32) A certain computation generates two arrays a and b such that a[i]=f(i) for 0 ≤ i < n and b[i]=g(a[i]) for 0 ≤ i < n. Suppose this computation is decomposed into two concurrent processes X and Y such that X computes the array a and Y computes the array b. The processes employ two binary semaphores R and S, both initialized to zero. The array a is shared by the two processes. The structures of the processes are shown below.
Which one of the following represents the CORRECT implementations of ExitX and EntryY?
a.
b.
c.
d.
Answer: c
Explanation:
The purpose here is neither the deadlock should occur nor the binary semaphores be assigned value greater than one.
A leads to deadlock
B can increase value of semaphores b / w 1 to n
D may increase the value of semaphore R and S to 2 in some cases
33) Consider the following two sets of LR(1) items of an LR(1) grammar.
X -> c.X, c / d
X -> .cX, c / d
X -> .d, c / d
X -> c.X, $
X -> .cX, $
X -> .d, $
Which of the following statements related to merging of the two sets in the corresponding LALR parser is/are FALSE?
- Cannot be merged since look aheads are different.
- Can be merged but will result in S-R conflict.
- Can be merged but will result in R-R conflict.
- Cannot be merged since goto on c will lead to two different sets.
- 1 only
- 2 only
- 1 and 4 only
- 1, 2, 3, and 4
Answer: d
Explanation:
The given two LR(1) set of items are :
X -> c.X, c / d
X -> .cX, c / d
X -> .d, c / d
and
X -> c.X, $
X -> .cX, $
X -> .d, $
The symbols/terminals after the comma are Look-Ahead symbols.
These are the sets of LR(1) ( LR(1) is also called CLR(1) ) items.
The LALR(1) parser combines those set of LR(1) items which are identical with respect to their 1st component but different with respect to their 2nd component.
In a production rule of a LR(1) set of items, ( A -> B , c ) , A ->B is the 1st component , and the Look-Ahead set of symbols, which is c here, is the second component.
Now we can see that in the sets given, 1st component of the corresponding production rule is identical in both sets, and they only differ in 2nd component ( i.e. their look-ahead symbols) hence we can combine these sets to make a a single set which would be :
X -> c.X, c/d/$
X -> .cX, c/d/$
X -> .d, c/d/$
This is done to reduce the total number of parser states.
Now we can check the statements given.
Statement 1 : The statement is false, as merging has been done because 2nd components i.e. look-ahead were different.
Statement 2 : In the merged set, we can't see any Shift-Reduce conflict ( because no reduction even possible, reduction would be possible when a production of form P -> q. is present)
Statement 3 : In the merged set, we can't see any Reduce-Reduce conflict ( same reason as above, no reduction even possible, so no chances of R-R conflict )
Statement 4: This statement is also wrong, because goto is carried on Non-Terminals symbols, not on terminal symbols, and c is a terminal symbol.
Thus, all statements are wrong, hence option D.
34) Which of the following is/are undecidable?
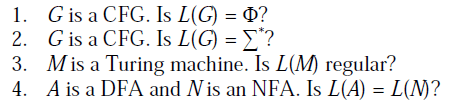
- 3 only
- 3 and 4 only
- 1, 2 and 3 only
- 2 and 3 only
Answer: d
Explanation:
- First is Emptiness for CFG; whether a CFG is empty or not, this problem is decidable.
- Second is everything for CFG; whether a CFG will generate all possible strings (completeness of CFG), this problem is undecidable.
- Third is Regularity for REC; whether language generated by TM is regular is undecidable.
- Fourth is equivalence for regular; whether language generated by DFA and NFA are same is decidable.
Second and third will be undecidable. Hence, option (D) is Correct.
35) What is the return value of f(p,p), if the value of p is initialized to 5 before the call? Note that the first parameter is passed by reference, whereas the second parameter is passed by value
- 3024
- 6561
- 55440
- 161051
Answer: b
Explanation:
Since c is passed by value and x is passed by reference, all functions will have same copy of x, but different copies of c.
f(5, 5) = f(x, 4) * x = f(x, 3) * x * x = f(x, 2) * x * x * x = f(x, 1) * x * x * x * x = 1 * x * x * x * x = x^4
Since x is incremented in every function call, it becomes 9 after f(x, 2) call. So the value of expression x^4 becomes 9^4 which is 6561.
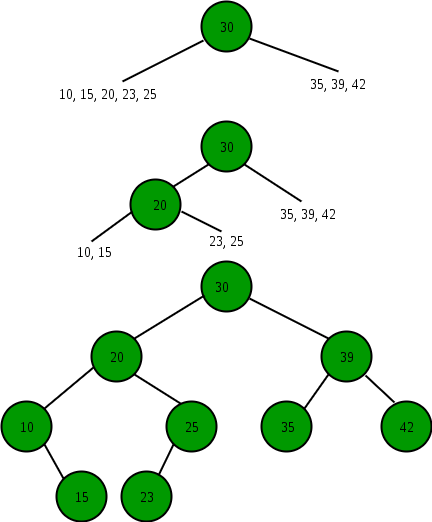
36) The preorder traversal sequence of a binary search tree is 30, 20, 10, 15, 25, 23, 39, 35, 42. Which one of the following is the postorder traversal sequence of the same tree?
- 10, 20, 15, 23, 25, 35, 42, 39, 30
- 15, 10, 25, 23, 20, 42, 35, 39, 30
- 15, 20, 10, 23, 25, 42, 35, 39, 30
- 15, 10, 23, 25, 20, 35, 42, 39, 30
Answer: d
Explanation:
In order to construct a binary tree from given traversal sequences, one of the traversal sequence must be Inorder. The other traversal sequence can be either Preorder or Postorder. We know that the Inorder traversal of Binary Search Tree is always in ascending order so the Inorder Traversal would be the ascending order of given Preorder traversal i.e 10, 15, 20, 23, 25, 30, 35, 39, 42.Now we have to construct a tree from given Inorder and Preorder traversals.
37) Consider the following operation along with Enqueue and Dequeue operations on queues, where k is a global parameter.
What is the worst case time complexity of a sequence of n MultiDequeue() operations on an initially empty queue?
(A) ⊝(n)
(B) ⊝(n + k)
(C) ⊝(nk)
(D) ⊝(nk2)
- A
- B
- C
- D
Answer: b
Explanation: Since the queue is empty initially, the condition of while loop never becomes true. So the time complexity is ⊝(n).
38) Consider an instruction pipeline with five stages without any branch prediction: Fetch Instruction (FI), Decode Instruction (DI), Fetch Operand (FO), Execute Instruction (EI) and Write Operand (WO). The stage delays for FI, DI, FO, EI and WO are 5 ns, 7 ns, 10 ns, 8 ns and 6 ns, respectively. There are intermediate storage buffers after each stage and the delay of each buffer is 1 ns. A program consisting of 12 instructions I1, I2, I3,. . . . . . . . I12 is executed in this pipelined processor. Instruction I4 is the only branch instruction and its branch target is I9. If the branch is taken during the execution of this program, the time (in ns) needed to complete the program is
- 132
- 165
- 176
- 328
Answer: b
Explanation:
Pipeline will have to be stalled till Ei stage of l4 completes, ss Ei stage will tell whether to take branch or not.
After that l4(WO) and l9(Fi) can go in parallel and later the following instructions.
So, till l4(Ei) completes : 7 cycles * (10 + 1 ) ns = 77ns
From l4(WO) or l9(Fi) to l12(WO) : 8 cycles * (10 + 1)ns = 88ns
Total = 77 + 88 = 165 ns
39) A RAM chip has a capacity of 1024 words of 8 bits each (1K × 8). The number of 2 × 4 decoders with enable line needed to construct a 16K × 16 RAM from 1K × 8 RAM is
- 4
- 5
- 6
- 7
Answer: b
Explanation:
RAM chip size = 1k × 8[1024 words of 8 bits each]
RAM to construct = 16k × 16
Number of chips required = (16k x 16) / ( 1k x 8) = (16 x 2)
[16 chips vertically with each having 2 chips horizontally]
So to select one chip out of 16 vertical chips, we need 4 x 16 decoder.
Available decoder is 2 x 4 decoder
To be constructed is 4 x 16 decoder
Hence 4 + 1 = 5 decoders are required.
40)
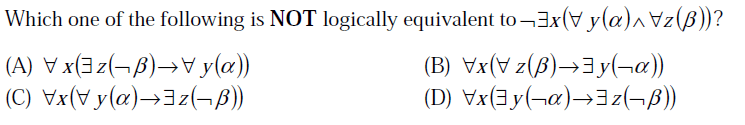
- A
- B
- C
- D
Answer: (A) (D)
Explanation:
Given statement is : ¬ ∃ x ( ∀ y(α) ∧ ∀ z(β) )
where ¬ is a negation operator, ∃ is Existential Quantifier with the meaning of "there Exists", and ∀ is a Universal Quantifier with the meaning " for all " , and α, β can be treated as predicates.
here we can apply some of the standard results of Propositional and 1st order logic on the given statement, which are as follows :
[ Result 1 : ¬(∀x P(x)) <=> ∃ x ¬P(x), i.e. negation of "for all" gives "there exists" and negation also gets applied to scope of quantifier, which is P(x) here. And also negation of "there exists" gives "for all", and negation also gets applied to scope of quantifier ]
[ Result 2 : ¬ ( A ∧ B ) = ( ¬A ∨ ¬B ) ] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -(1)
[ Result 3 : ¬P ∨ Q <=> P -> Q ] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (2)
[ Result 4 : If P -> Q, then by Result of Contrapositive, ¬Q -> ¬P ]
Now we need to use these results as shown below:
¬ ∃ x ( ∀y(α) ∧ ∀z(β) ) - - - - - - - - - - - - - - - - - - - - - [ Given ]
=> ∀ x (¬∀y(α) ∨ ¬∀z(β) ) - - - - - - - - - - - - - - - - - [ after applying Result 1 & Result 2 ]
=> ∀ x ( ∀y(α) -> ¬∀z(β) ) - - - - - - - - - - - - - - - - -[after applying Result 3 ]
=> ∀ x ( ∀ y(α) -> ∃ z(¬β) ) - - - - - - - - - - - - - - - - -[after applying Result 1] which is same as the statement C.
Hence the Given Statement is logically Equivalent to the statement C.
Now, we can also prove that given statement is logically equivalent to the statement in option B.
Let's see how !
The above derived statement is
∀ x ( ∀y(α) -> ∃z(¬β) )
Now this statement can be written as (or equivalent to) :
=> ∀ x ( ∀ z(β) -> ∃ y(¬α) ) - - - - - - - - - - - - - - - - - - - - - - - - - -[after applying Result 4]
And this statement is same as statement B.
Hence the Given statement is also logically equivalent
to the statement B.
So, we can conclude that the Given statement is NOT logically equivalent to the
statements A and D.
Hence, the correct answer is Option A and Option D. But in GATE 2013, marks were given to all for this question.
41) The following code segment is executed on a processor which allows only register operands in its instructions. Each instruction can have atmost two source operands and one destination operand. Assume that all variables are dead after this code segment.
Suppose the instruction set architecture of the processor has only two registers. The only allowed compiler optimization is code motion, which moves statements from one place to another while preserving correctness. What is the minimum number of spills to memory in the compiled code?
- 0
- 1
- 2
- 3
Answer: b
Explanation:
r1. . . . . . . r2
a. . . . . . . b . . . . . . . c = a + b
a. . . . . . . x = c * c
a.......x......but we will have to store c in mem as we don't know if x > a . . . . . . . or not
y.......x......y = a * a
choosing the best case of x > a , min spills = 1
42) Consider the same data as above question. What is the minimum number of registers needed in the instruction set architecture of the processor to compile this code segment without any spill to memory? Do not apply any optimization other than optimizing register allocation.
- 3
- 4
- 5
- 6
Answer: b
Explanation:
Note that for solving the above problem we are not allowed for code motion.
So, we will start analysing the code line by line and determine how many registers will be required to execute the above code snippet.
Assuming the registers are numbered R1, R2, R3 and R4. The analysis has been shown in the table below
| Statement | Registers Used |
|---|---|
| c = a + b | R2 <- R1 + R2 |
| d = c * a | R3 <- R2 * R1 |
| e = c + a | R4 <- R1 + R2 |
| x = c * c | R2 <- R2 * R2 |
| If( x > a) { | Here we compare R2 and R1 |
| y = a * a | R1 <- R1 * R2 |
| } | |
| else { | |
| d = d * d | R3 <- R3 + R3 |
| e = e * e | R4 <- R4 * R4 |
| } |
So from the above analysis we can conclude that we will need minimum 4 registers to execute the above code snippet.
43) The procedure given below is required to find and replace certain characters inside an input character string supplied in array A. The characters to be replaced are supplied in array oldc, while their respective replacement characters are supplied in array newc. Array A has a fixed length of five characters, while arrays oldc and newc contain three characters each. However, the procedure is flawed
The procedure is tested with the following four test cases
(1) oldc = "abc", newc = "dab"
(2) oldc = "cde", newc = "bcd"
(3) oldc = "bca", newc = "cda"
(4) oldc = "abc", newc = "bac"
The tester now tests the program on all input strings of length five consisting of characters 'a', 'b', 'c', 'd' and 'e' with duplicates allowed. If the tester carries out this testing with the four test cases given above, how many test cases will be able to capture the flaw?
- Only one
- Only Two
- Only Three
- All Four
Answer: b
Explanation: The test cases 3 and 4 are the only cases that capture the flaw. The code doesn't work properly when an old character is replaced by a new character and the new character is again replaced by another new character. This doesn't happen in test cases (1) and (2), it happens only in cases (3) and (4).
44) In the above question, if array A is made to hold the string "abcde", which of the above four test cases will be successful in exposing the flaw in this procedure?
- None
- 2 Only
- 3 and 4 only
- 4 only
Answer: c
Explanation:
Test Case 1
abcde
abbcd
Test Case 2
abcde
addde
Test Case 3
abcde
aacde
45) A computer uses 46-bit virtual address, 32-bit physical address, and a three-level paged page table organization. The page table base register stores the base address of the first-level table (T1), which occupies exactly one page. Each entry of T1 stores the base address of a page of the second-level table (T2). Each entry of T2 stores the base address of a page of the third-level table (T3). Each entry of T3 stores a page table entry (PTE). The PTE is 32 bits in size. The processor used in the computer has a 1 MB 16-way set associative virtually indexed physically tagged cache. The cache block size is 64 bytes.
What is the size of a page in KB in this computer?
- 2
- 4
- 8
- 16
Answer: c
Explanation:
Let the page size is of 'x' bits Size of T1 = 2 ^ x bytes
(This is because T1 occupies exactly one page)
Now, number of entries in T1 = (2 ^ x) / 4(This is because each page table entry is 32 bits or 4 bytes in size)
Number of entries in T1 = Number of second level page tables(Because each I-level page table entry stores the base address of page of II-level page table)
Total size of second level page tables = ((2 ^ x) / 4) * (2 ^ x)
Similarly, number of entries in II-level page tables = Number of III level page tables = ((2 ^ x) / 4) * ((2 ^ x) / 4)
Total size of third level page tables = ((2 ^ x) / 4) * ((2 ^ x) / 4) * (2 ^ x)
Similarly, total number of entries (pages) in all III-level page tables = ((2 ^ x) / 4) * ((2 ^ x) / 4) * ((2 ^ x) / 4) = 2^(3x - 6)
Size of virtual memory = 2 ^ 46
Number of pages in virtual memory = (2 ^ 46) / (2 ^ x) = 2 ^ (46 - x)
Total number the pages in the III-level page tables = Number of pages in virtual memory 2 ^ (3x - 6) = 2 ^ (46 - x)
3x - 6 = 46 - x => 4x = 52 => x = 13
That means, page size is of 13 bits or Page size = 2 ^ 13 bytes = 8 KB
46) Consider the same data as above question. What is the minimum number of page colours needed to guarantee that no two synonyms map to different sets in the processor cache of this computer?
- 2
- 4
- 8
- 16
Answer: c
Explanation:
1 MB 16-way set associative virtually indexed physically tagged cache(VIPT).
The cache block size is 64 bytes.
No of blocks is 2 ^ 20 / 2 ^ 6 = 2 ^ 14.
No of sets is 2 ^ 14 / 2 ^ 4 = 2 ^ 10.
VA(46)
+- - - - - - - - - - - - - - - - -+
tag(30) , Set(10) , block offset(6)
+- - - - - - - - - - - - - - - - -+
In VIPT if the no. of bits of page offset = (Set + block offset) then only one page color is sufficient.
but we need 8 colors because the number bits where the cache set index and physical page number overlap is 3 so 2 ^ 3 page colors is reuired.
Hence option c is ans.
47) Relation R has eight attributes ABCDEFGH. Fields of R contain only atomic values. F = {CH → G, A → BC, B → CFH, E → A, F → EG} is a set of functional dependencies (FD's) so that F + is exactly the set of FD's that hold for R.
Consider the FDs given in above question. The relation R is
- in 1NF, but not in 2NF.
- in 2NF, but not in 3NF.
- in 3NF, but not in BCNF.
- in BCNF
Answer: a
Explanation:
Lets calculate the candidate key using relational schema R(A, B, C, D, E, F, G, H) and FD's F = {CH → G, A → BC, B → CFH, E → A, F → EG}
Using RHS of all FD's we deduced that D has not been determined by any of the given FD's present, hence its sure that attribute D will surely be the part of all possible existing candidates key.
- Calculate closure of D i.e. D+ = D - - - - - - - - - - - (a)
- Calculate closure of D i.e. DA+ = D A B C F H E G - - - - - - - - - - - (b)
- Calculate closure of D i.e. DB+ = D B C F H E G A - - - - - - - - - - - (c)
- Calculate closure of D i.e. DC+ = DC - - - - - - - - - - - (d)
- Calculate closure of D i.e. DE+ = D E A B C F H G - - - - - - - - - - - (e)
- Calculate closure of D i.e. DF+ = D F E G A B C H - - - - - - - - - - - (f)
- Calculate closure of D i.e. DG+ = DG - - - - - - - - - - - (g)
- Calculate closure of D i.e. DH+ = DH - - - - - - - - - - - (h)
The candidate keys are AD, BD, ED and FD. As per definition of second normal form, No non-prime attribute should be partially dependent on key of a table. The table is not in 2nd Normal Form as the non-prime attributes are dependent on subsets of candidate keys.
The candidate keys are AD, BD, ED and FD. In all of the following FDs, the non-prime attributes are dependent on a partial candidate key.
A -> BC
B -> CFH
F -> EG.
48) Which one of the following options is the closest in meaning to the word given below?
Nadir
- Highest
- Lowest
- Medium
- Integration
Answer: b
Explanation:
Nadir means below
1. Astronomy A point on the celestial sphere directly below the observer, diametrically opposite the zenith.
2. The lowest point: the nadir of their fortunes.
49) Complete the sentence:
Universalism is to particularism as diffuseness is to _________________
- specificity
- neutrality
- generality
- adaptation
Answer: a
Explanation: Diffuseness means to spreading widely.
50) What will be the maximum sum of 44, 42, 40, . . . . . . . .?
- 502
- 504
- 506
- 500
Answer: c
Explanation:
This is a decreasing arithmetic progression with absolute difference as 2. The series is 44, 42, 40 . . . . . . . . . 0, -2, -4 . . . . . . .
The sum would be maximum if we consider the series till 0 or 2.
So sum would be 506 using the AP Sum formula.
51) Were you a bird, you ______________ in the sky.
- would fly
- shall fly
- should fly
- shall have flown
Answer: a
Explanation:
Were you a bird, you would fly in the sky.
Conditional Clause and Main Clause

First, Second, and Third Conditional
| 1. First conditional: | If I have enough money, I will go to Japan. |
| 2. Second conditional: | If I had enough money, I would go to Japan. |
| 3. Third conditional: | If I had had enough money, I would have gone to Japan. |
| Conditional clause | Main clause |
| 1. If + Present Tense | will + inf / present tense / imperative |
|
|
| 2. If + Past Tense | would + inf |
| 3. If + Past Perfect Tense | would have + past participle |
|
We do not normally use will or would in the conditional clause, |
|
Uses of the Conditional
First conditional
- Nature: Open condition, what is said in the condition is possible.
- Time: This condition refers either to present or to future time.
g. If he is late, we will have to go without him.
If my mother knows about this, we are in serious trouble.
Second conditional
- Nature: unreal (impossible) or improbable situations.
- Time: present; the TENSE is past, but we are talking about the present, now.
g. If I knew her name, I would tell you.
If I were you, I would tell my father.
Compare:If I become president, I will change the social security system. (Said by a presidential candidate)
If I became president, I would change the social security system. (Said by a schoolboy: improbable)
If we win this match, we are qualified for the semifinals.
If I won a million pounds, I would stop teaching. (improbable)
Third conditional
- Nature: unreal
- Time: Past (so we are talking about a situation that was notso in the past.) e.g. If you had warned me, I would not have told your father about that party.(But you didn't, and I have).
52) Choose the grammatically INCORRECT sentence:
- He is of Asian origin.
- They belonged to Africa.
- She is an European.
- They migrated from India to Australia.
Answer: c
Explanation:
The correct sentence is "She is a European."
'an' applies to those words which get pronounced with a, e, i, o, u.
Here pronunciation is "Yuropean" ( E-silent; has a "Y" sound) , similar to ' a University'.
Hence a European.
53) Find the sum of the expression
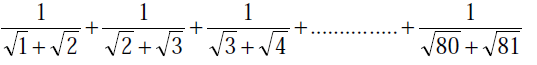
- 7
- 8
- 9
- 10
Answer: b
Explanation:
(√ 2 - √ 1) / (√ 2 + √ 1) (√ 2 - √ 1) + (√ 3 - √ 2) / (√ 2 + √ 2) (√ 3 - √2) + . . . . . . . . . . . . .
which simplifies to
(√ 2 - √ 1) + (√ 3 -√ 2) + . . . . . . . . (√ 81 - √ 80)
which again simplifies to: √81 - √1 which is 8
54) Out of all the 2-digit integers between 1 and 100, a 2-digit number has to be selected at random. What is the probability that the selected number is not divisible by 7?
- 13 / 90
- 12 / 90
- 78 / 90
- 77 / 90
Answer: d
Explanation:
There are total 90 two digit numbers, out of them 13 are divisible by 7, these are 14, 21, 28, 35, 42, 49, 56, 63, 70, 77, 84, 91, 98.
Therefore, probability that selected number is not divisible by 7 = 1 - 13 / 90 = 77/ 90.
So, option (D) is true.
55) After several defeats in wars, Robert Bruce went in exile and wanted to commit suicide. Just before committing suicide, he came across a spider attempting tirelessly to have its net. Time and again, the spider failed but that did not deter it to refrain from making attempts. Such attempts by the spider made Bruce curious. Thus, Bruce started observing the near-impossible goal of the spider to have the net. Ultimately, the spider succeeded in having its net despite several failures. Such act of the spider encouraged Bruce not to commit suicide. And then, Bruce went back again and won many a battle, and the rest is history.
Which one of the following assertions is best supported by the above information?
- Failure is the pillar of success.
- Honesty is the best policy.
- Life begins and ends with adventures.
- No adversity justifies giving up hope.
Answer: d
Explanation: None of A, B and C make sense.
Only option D "No adversity justifies giving up hope" is related to the given information.
56) A tourist covers half of his journey by train at 60 km/h, half of the remainder by bus at 30 km/h and the rest by cycle at 10 km/h. The average speed of the tourist in km/h during his entire journey is
- 36
- 30
- 24
- 18
Answer: c
Explanation: Let total distance be D
Total Time = D(1 / 2 * 60 + 1 / 4 * 30 + 1 / 4 * 10) = D / 24
Average Speed = Total distance / Total time = 24
57) The current erection cost of a structure is Rs. 13,200. If the labour wages per day increase by 1 / 5 of the current wages and the working hours decrease by 1 / 24 of the current period, then the new cost of erection in Rs. is
- 16,500
- 15,180
- 11,000
- 10,120
Answer: b
Explanation: Cost is proportional to wages per day and number of hours.
Wages are increased by 1 / 5 and working hours are decreased by 1 / 24.
So the cost becomes ( current cost ) * ( 1 + 1 / 5) * (1 - / 24) = 13200 * (6 / 5) * (23 / 24) = 15180
58) Consider the given graph
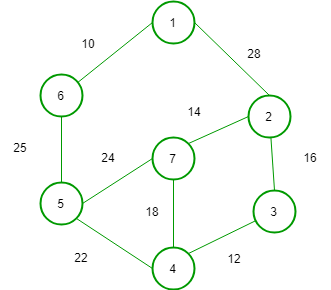
Its Minimum Cost Spanning Tree is __________.
(1)
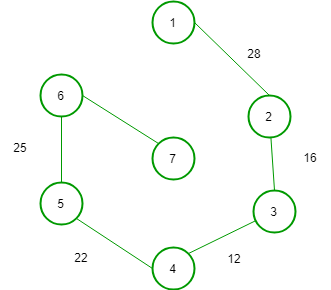
(2)
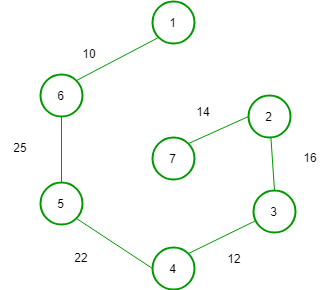
(3)
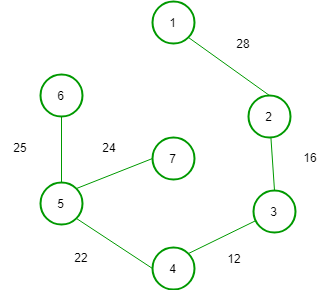
(4)
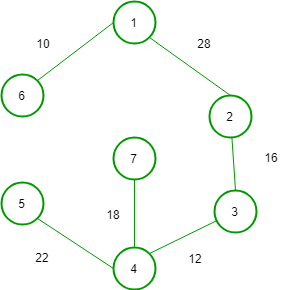
- (1)
- (2)
- (3)
- (4)
Answer: b
Explanation:
A minimum spanning tree (MST) or minimum weight spanning tree for a weighted, connected and undirected graph is a spanning tree with weight less than or equal to the weight of every other spanning tree.
In option (A) weight of tree is = 103 but it is not the subgraph from graph because in original graph there is no edge between node(6) and (7).
In option (B) weight of tree is = 99
In option (C) weight of tree is = 127
In option (D) weight of tree is = 106
So, option (B) is correct.
You may be interested in:
>> Is a Chromebook worth replacing a Windows laptop?
>> Find out in detail the outstanding features of Google Pixel 4a
>> Top 7 best earbuds you should not miss
Related Posts:
>> Recognizing 12 Basic Body Shapes To Choose Better Clothes
>>Ranking the 10 most used smart technology devices
>> Top 5+ Best E-readers: Compact & Convenient Pen

0 Comments:
Post a Comment