 A new trend in social engineering and impersonation emerges as cybercriminals take advantage of a user’s inability to properly identify fake corporate logos in phishing attacks.
A new trend in social engineering and impersonation emerges as cybercriminals take advantage of a user’s inability to properly identify fake corporate logos in phishing attacks.
We’ve all seen the really bad impersonation phishing email attempts – you know the one’s where you can immediately tell it’s not the vendor it purports to be from. And then there’s the really good ones that look perfect. But one of the needs most phishing attacks have is a need to display graphics so copied logos and branding can be displayed in order to fool the recipient.
But security researchers at anti-phishing vendor Inky have spotted an attack where scammers attempting to impersonate Verizon use symbols to represent the “check” portion of the logo, making the entirety of the “logo” appear without the need for downloading images.
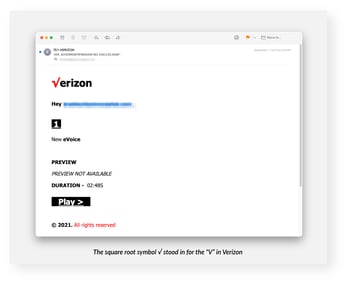
Source: Inky
You may think, “come on… that doesn’t even look like the Verizon logo at all!” and you’d be right. But new branding research around how well consumers memorize corporate logos correctly shows that most people actually remember a version of the logo enough to recognize it, but most don’t actually know exactly what the logo looks like. Using ten of the most well-known brands, it was concluded that, at best, 30% of people can draw a near-perfect version of the logo, with the average being only 16.6% of people.
This means that it’s far more likely than you think that if a phishing scammer can use some rendition of a logo, it may just be enough to fool them into thinking it’s the company they are attempting to impersonate.
Users that undergo Security Awareness Training are far less likely to fall for phishing attacks, regardless of how spot-on the impersonation. By reinforcing the need to scrutinize unsolicited and unexpected emails for sender details, content, type of request, and – yes – branding, it’s possible to spot nearly every phish a mile away.
You may be interested in:
>> Is a Chromebook worth replacing a Windows laptop?
>> Find out in detail the outstanding features of Google Pixel 4a
>> Top 7 best earbuds you should not miss
Related Posts:
>> Recognizing 12 Basic Body Shapes To Choose Better Clothes
>>Ranking the 10 most used smart technology devices
>> Top 5+ Best E-readers: Compact & Convenient Pen

0 Comments:
Post a Comment